Enable SAML SSO with Azure Active Directory
SAML SSO is a paid offering. Please contact the MacStadium Support team or your Account Manager to confirm eligibility to enable SAML SSO.
Please note that we do not currently support IdP-initiated logins. After SSO is configured with MacStadium, all users will use the below link to log into your account using an ID that will be provided to you by the MacStadium team.
https://portal.macstadium.com/sso
- Open Entra ID admin
- Navigate to “Enterprise applications”
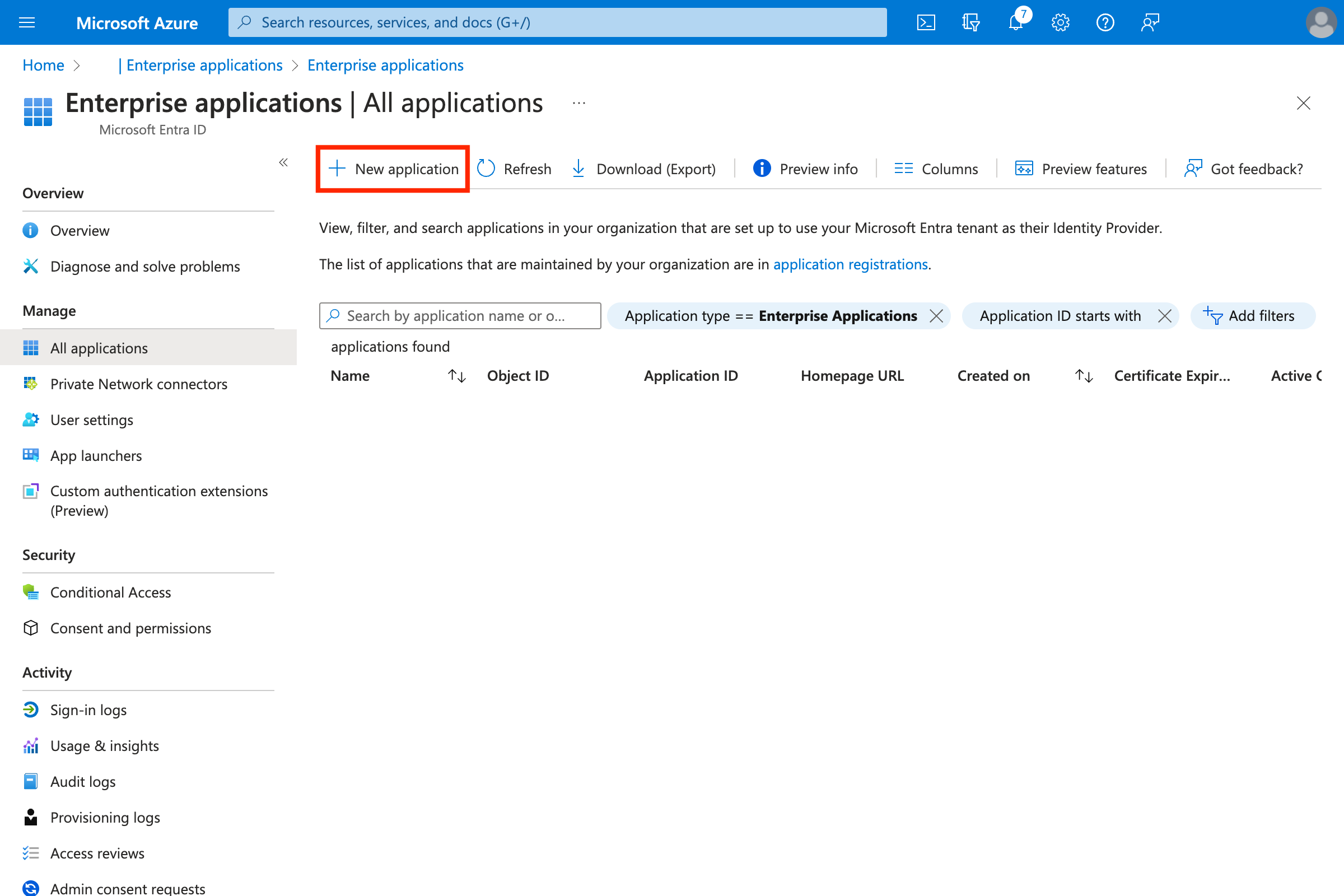
- Create a new application (click New application)
- Create your own application (click Create your own application)
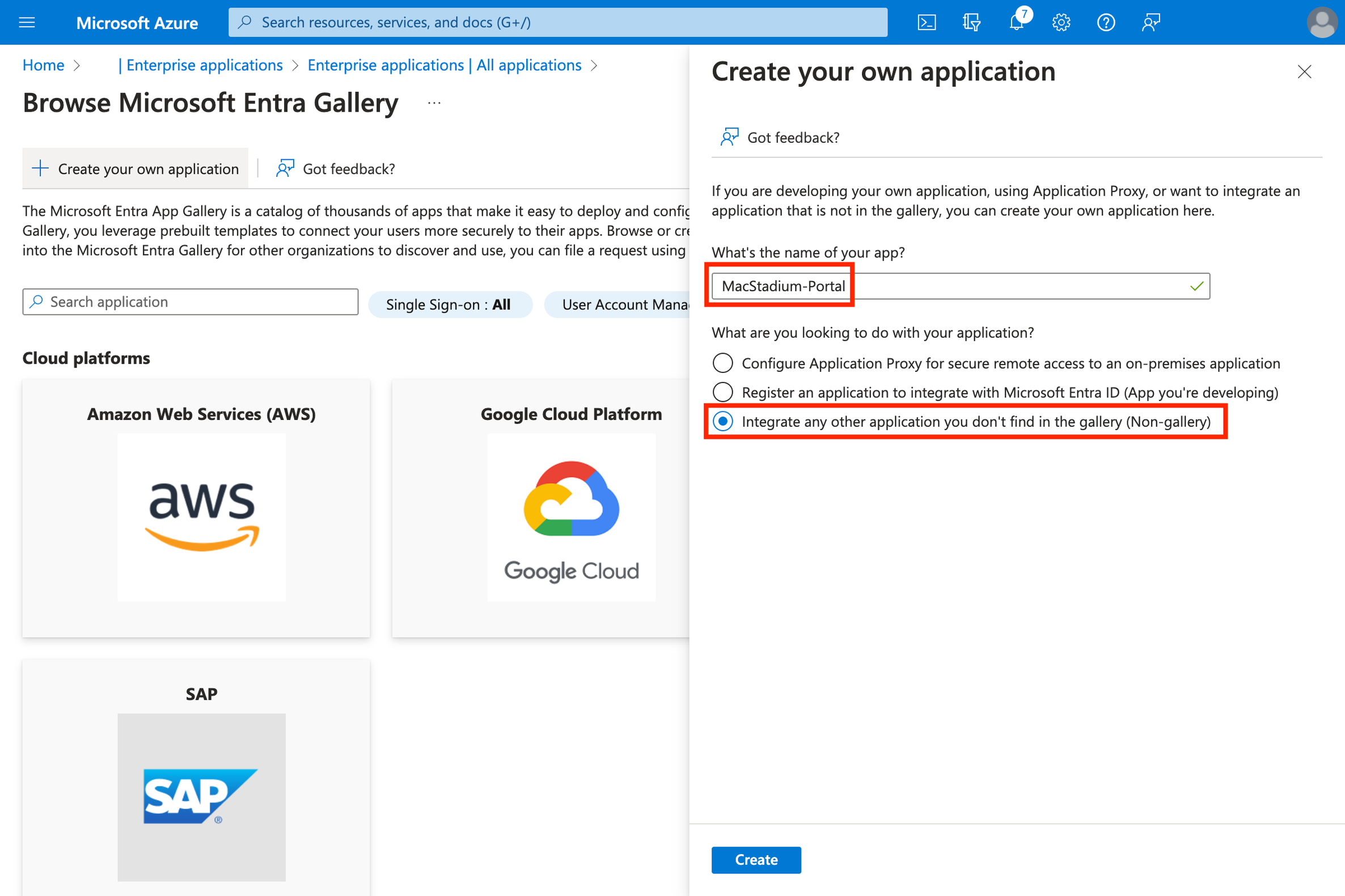
a. Enter name (e.g. “MacStadium-Portal”)
b. Select “Integrate any other application you don’t find in the gallery (Non-gallery)”
- Click “Single sign-on”
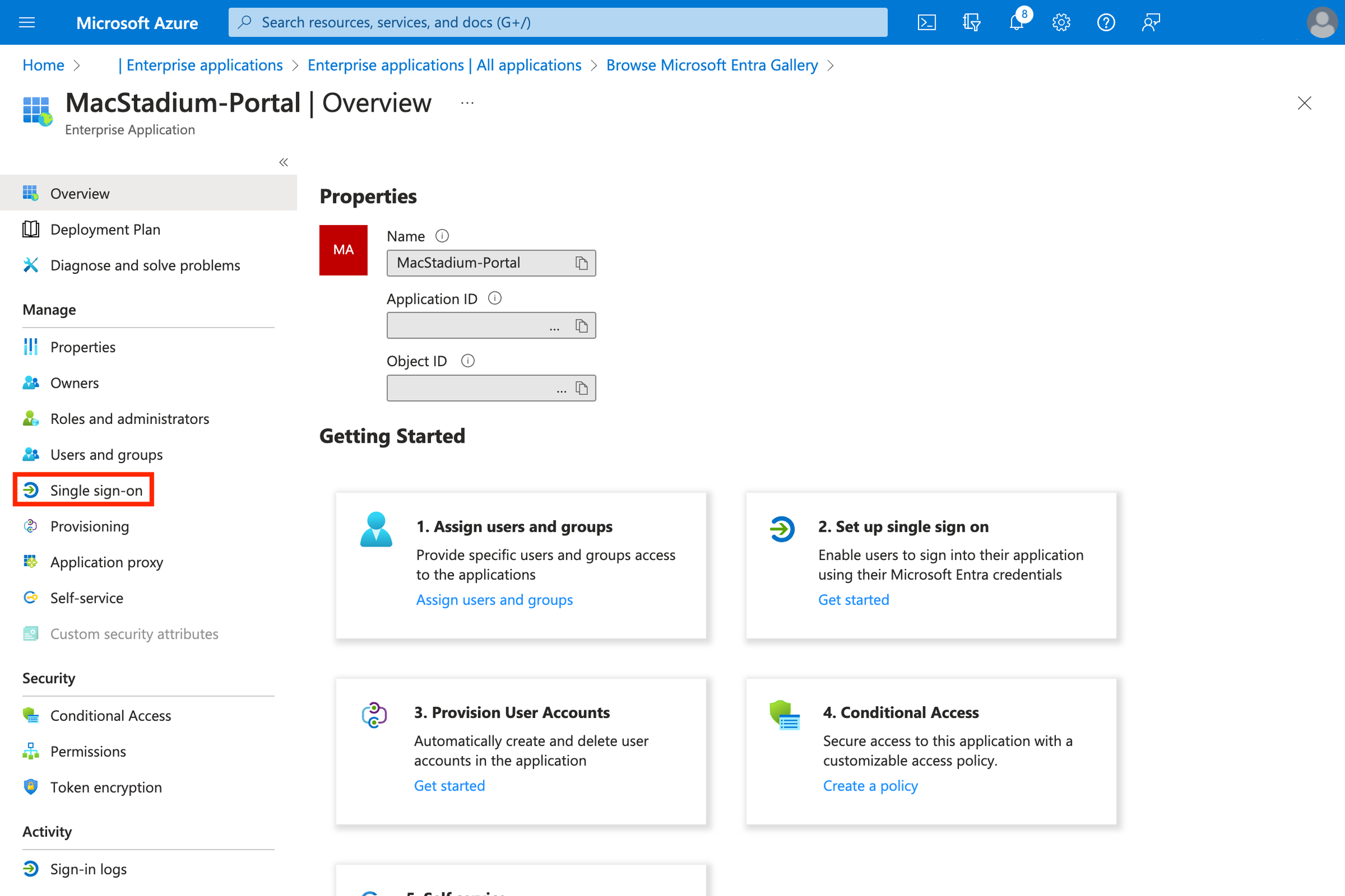
- Select “SAML”
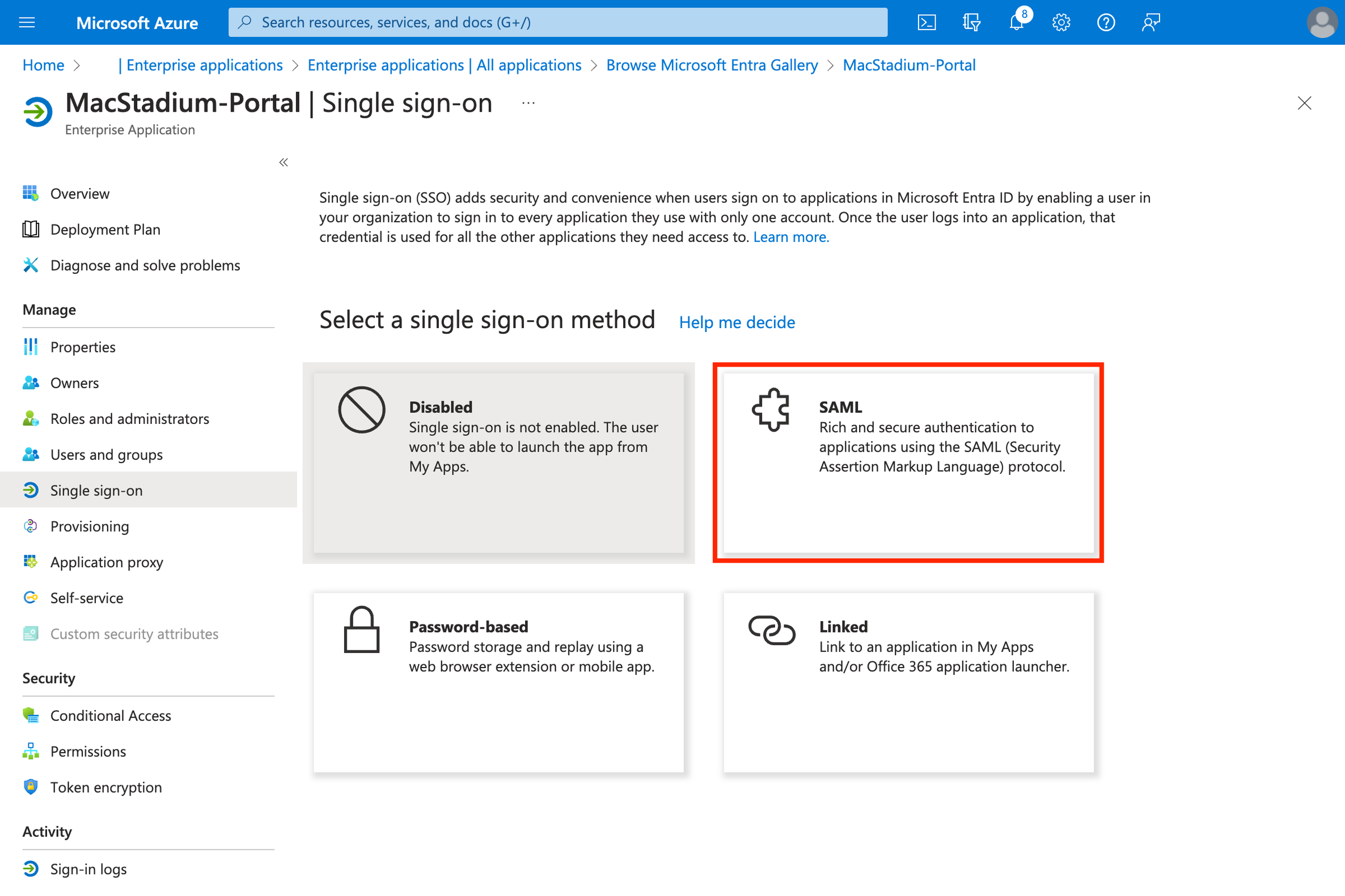
- Click “Edit” on the “Basic SAML settings”
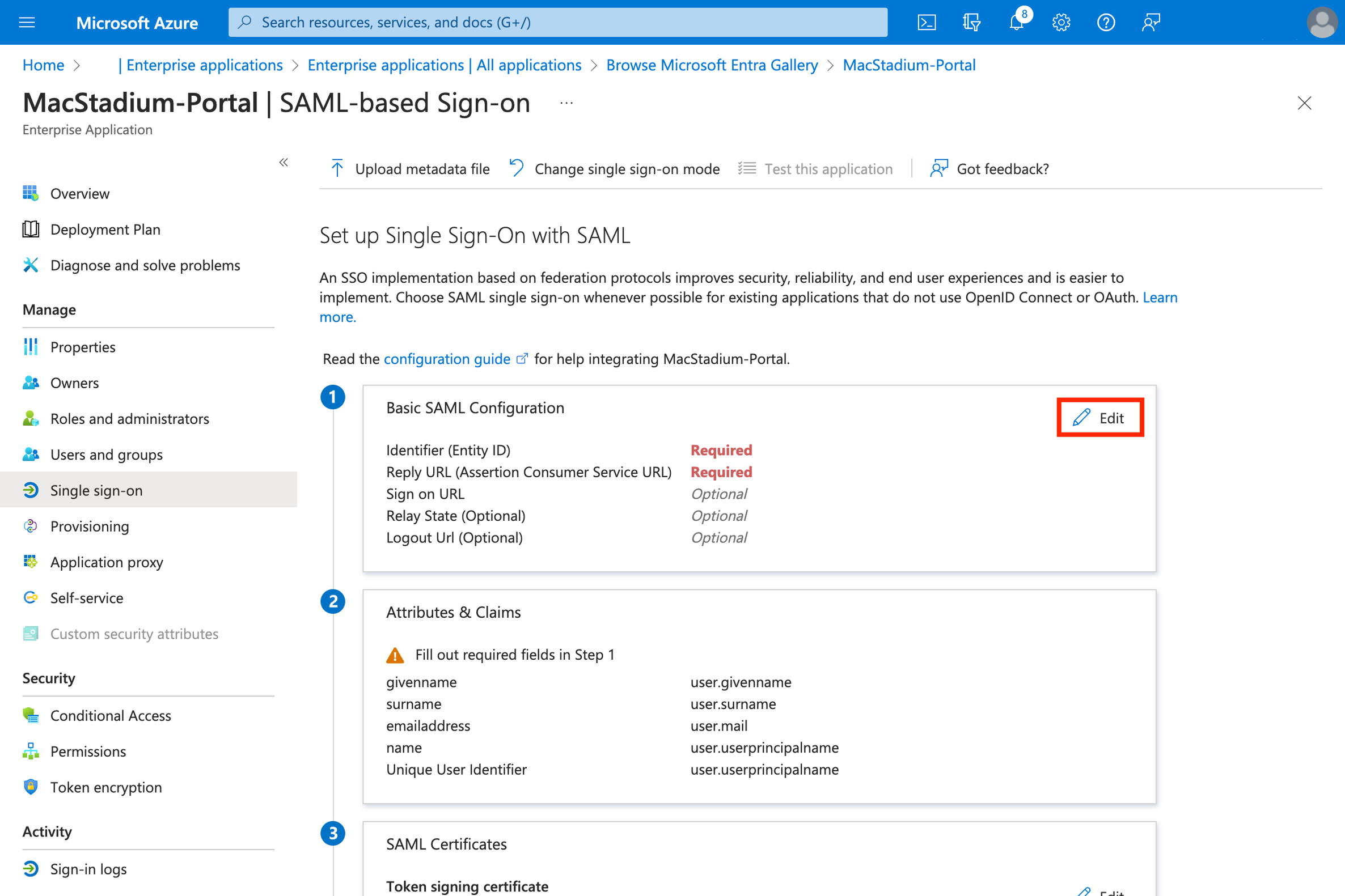
-
Configure SAML
- Identifier (Entity ID):
urn:amazon:cognito:sp:us-east-1_pusi8jHs1 - Reply URL (Assertion Consumer Service URL):
https://idp.macstadium.com/saml2/idpresponse - Logout URL (Optional):
https://idp.macstadium.com/saml2/logout - Complete the setup by clicking “Save”
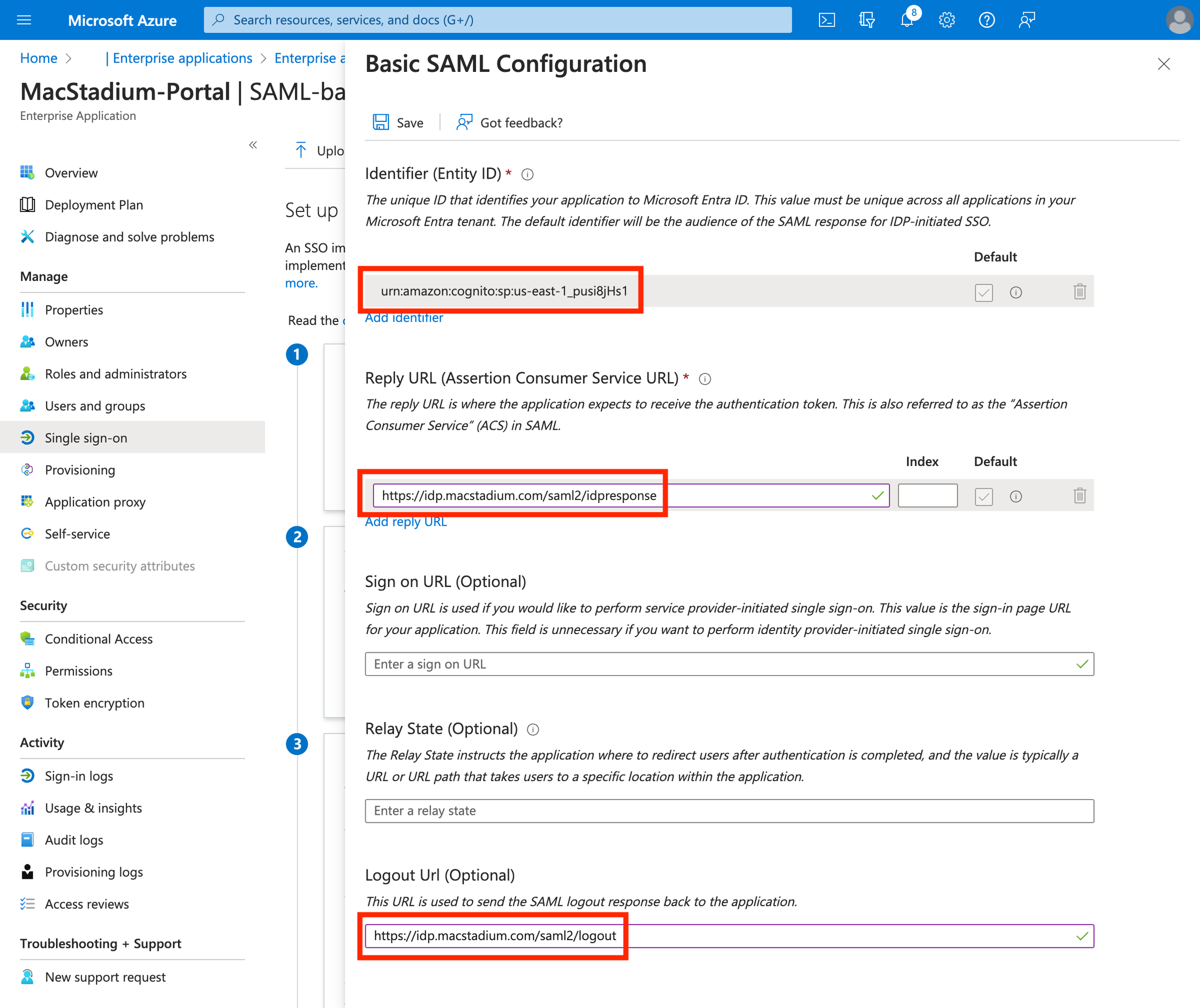
- Identifier (Entity ID):
-
IMPORTANT: Next, edit the Attributes & Claims for your SAML app. You will need the email field to be mapped to user.mail.
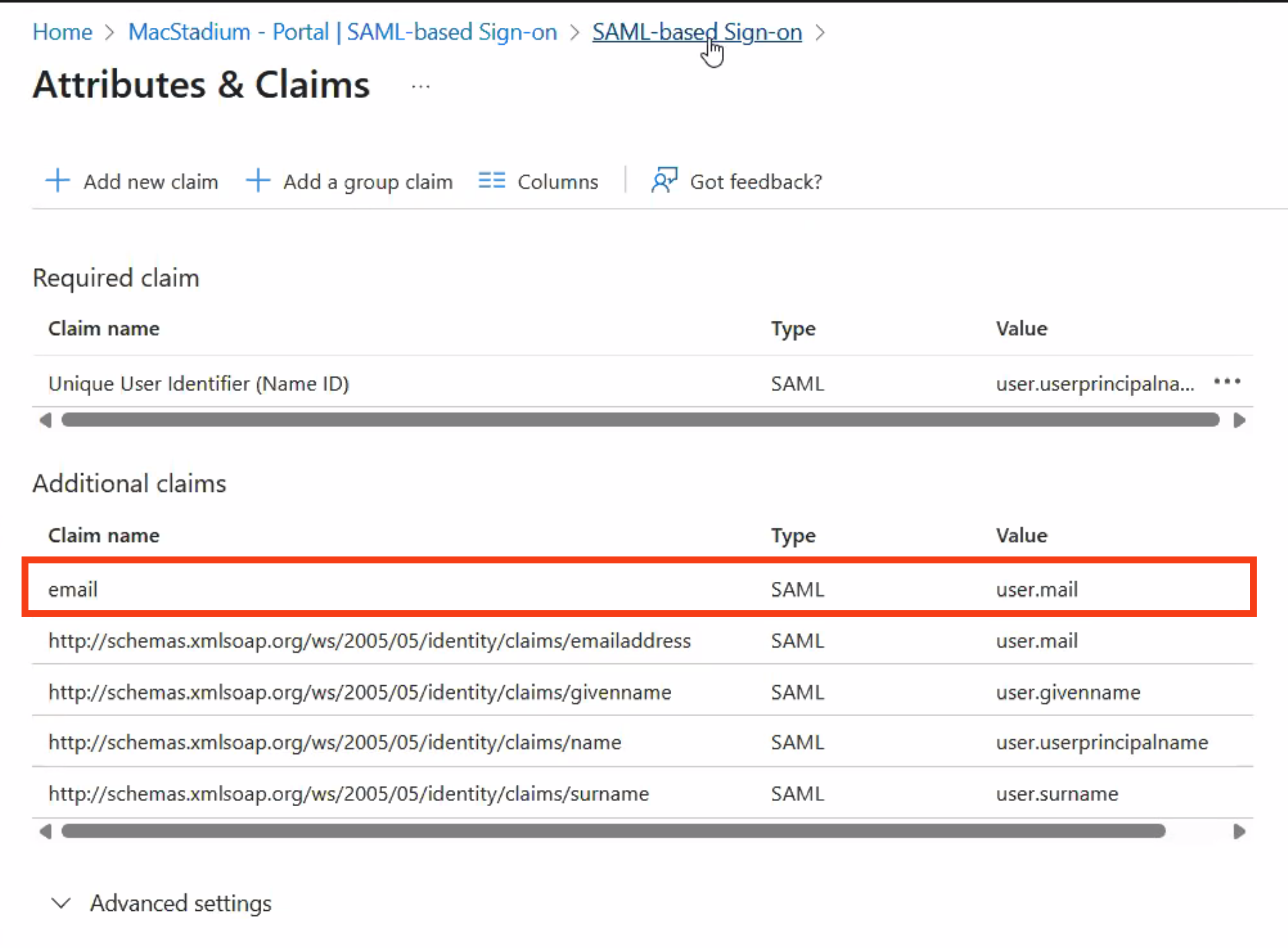
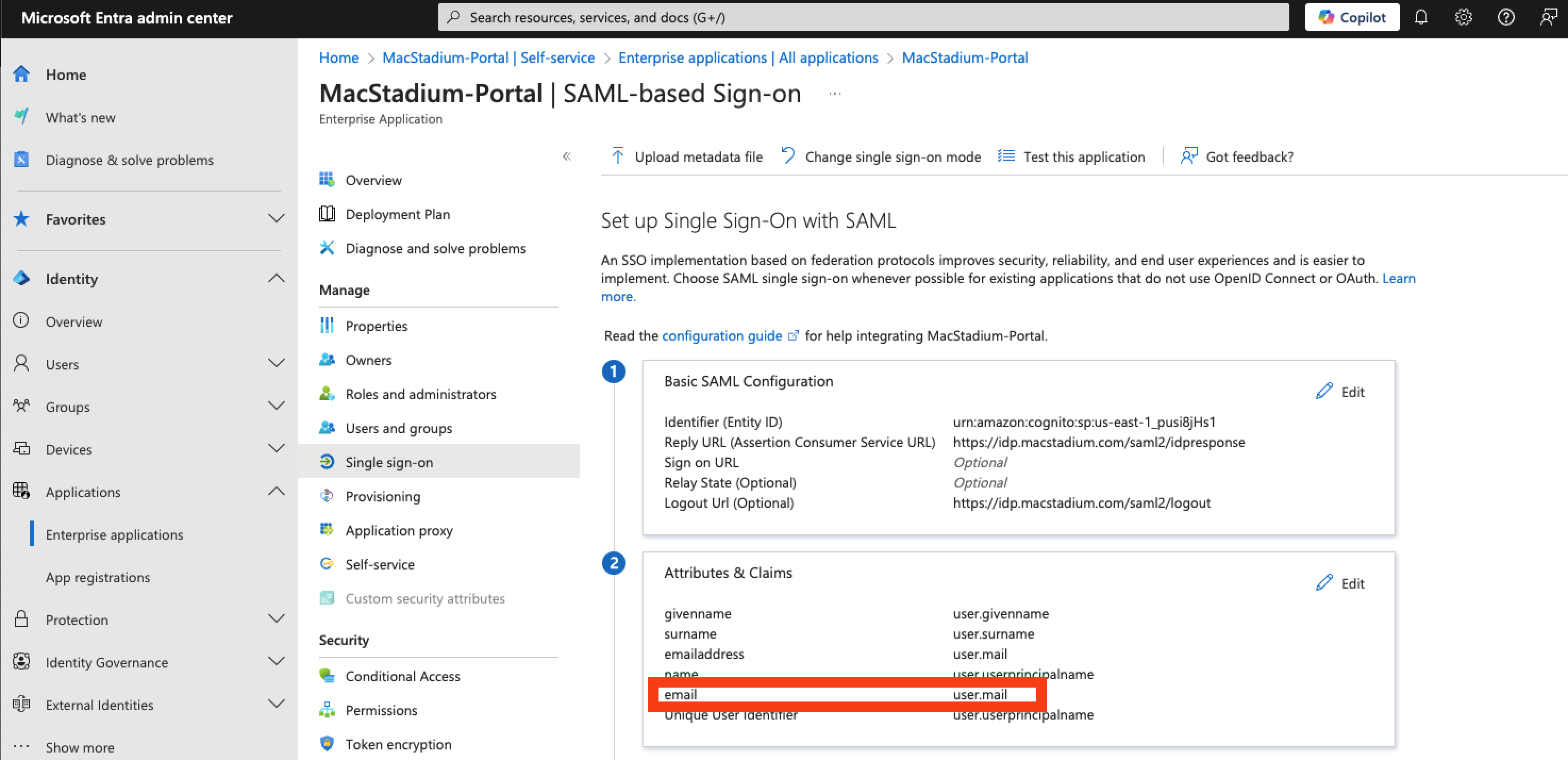
Once configured properly, section 2 of your SAML app should look like the below screenshot.
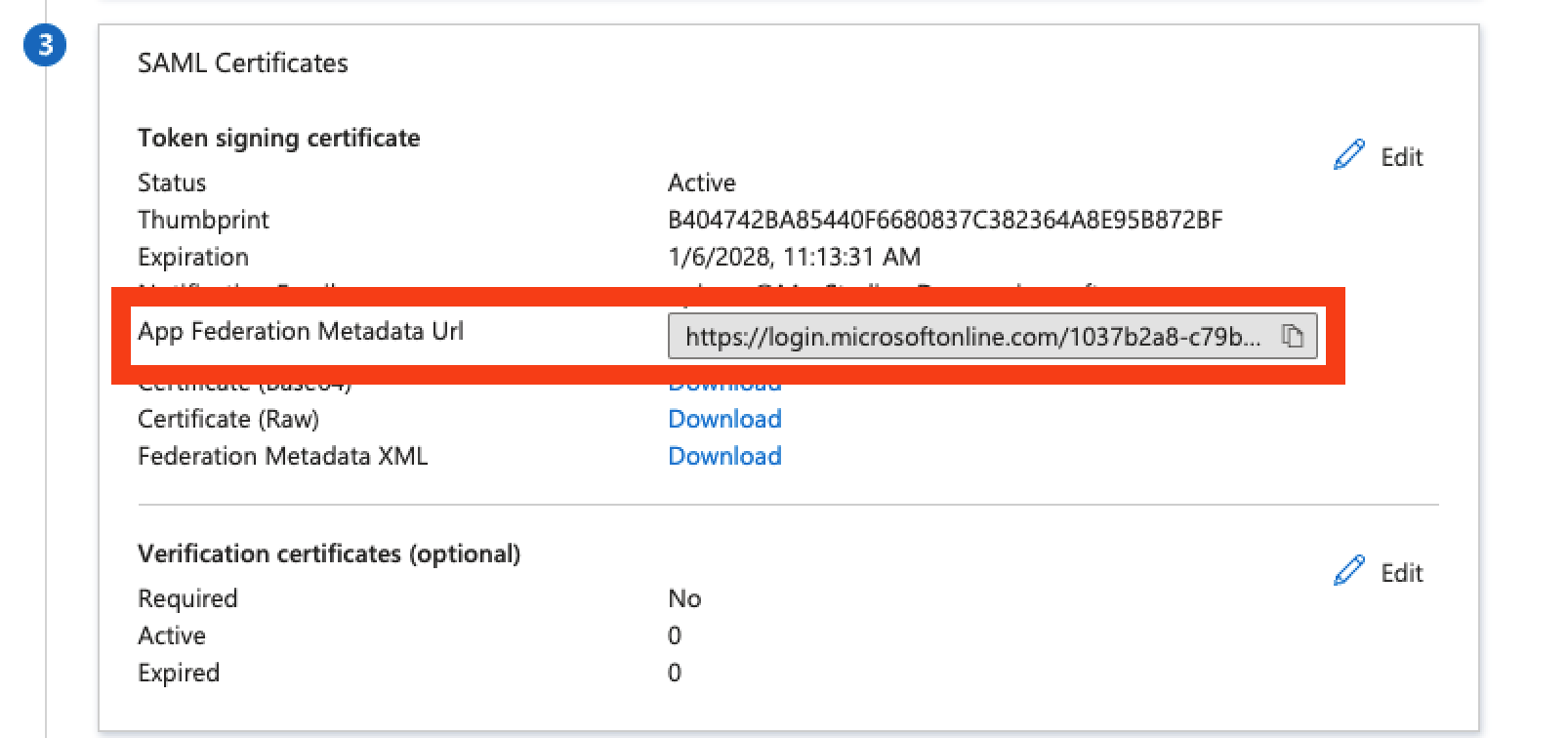
Once the attributes & claims are updated, please provide our support team with the app federation metadata URL. You can copy the federation metadata URL in section 3 of your SAML app, as shown in the below screenshot.
Updated 3 months ago
