Enable SAML SSO with Okta
Overview
In this article, you'll learn how to set up SAML SSO with Okta, allowing you to:
- Enable your users to be automatically signed in to MacStadium using their Okta accounts.
- Manage your accounts in one central location – Okta.
SAML SSO is a paid offering. Contact the MacStadium Support team or your Account Manager to confirm eligibility to enable SAML SSO.
Please note that we do not currently support IdP-initiated logins. After SSO is configured with MacStadium, all users will use the below link to log into your account using an ID that will be provided to you by the MacStadium team.
https://portal.macstadium.com/sso
Steps
- Save our public signature key below (e.g. save to
macstadium-us-east-1_pusi8jHs1.pem).
-----BEGIN CERTIFICATE-----
MIICvDCCAaSgAwIBAgIIdQAHcexaNC4wDQYJKoZIhvcNAQELBQAwHjEcMBoGA1UEAwwTdXMtZWFzdC0xX3B1c2k4akhzMTAeFw0yNDAxMTAxNDEzMThaFw0zNDAxMTAwMDI1MThaMB4xHDAaBgNVBAMME3VzLWVhc3QtMV9wdXNpOGpIczEwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDiLAh9YbRaJFwq6wODIsJixW9sCPVbO6MRwtSXEqDp1oRuJ//c7DVsytJd3koj1WRtF9+Hg1lvhx9Of+D0l5hjltB4mbeaQpOxcwgdxCepba2OuzxpU4APOCyU++NBfqe3Be+GIkWnbygsYFo5Dq26dFTSzYq/UNamYBTRgPh28k3yv82A2cH96wqwWGuLg52TUc56AGSCAwTCqN5VlwNaMzAuYqxHW2zotmeLtC9T8q0vS+/UWq/EckR7jV/R4ziyEYB/PWgkZNUnOp0TCYtiuoYdHuqzoazWjhQjil9W0TsUq6k6Vo2ISz+r3XxlXXQMk6blmfJDU7JcMEkPZybhAgMBAAEwDQYJKoZIhvcNAQELBQADggEBAJ8QzPsFgF/prkw2/qsgfAs0nKJY+zAaIqYSGZlYY4pqpObs0q2O8R3ecsS8e1cpahn4GdstPad69CqgyqPVf7EZm5ZMfUY9s5P7ufDJ3neh/YTp6KX1yHG8PJwJuCPSbB6OxcQirrxOKwsT2tPUMOziYHPQuickpJ7WlxEso3XjQlcU+F4L8tjhxxF3/T7+fOlzZmivLcBPVx7z+21VoARhJvetoqCqzRccrOitHWyeBma/C6JOtvFq3JPWH0rgmAV6IGhvCSro4ANaToEmK7JYXiOD13DlA44P0l6gV7L8p5EbQgF1F9eBQpfvL2E3Ml/+ZrXf5zBr5EjSLKvj/NE=
-----END CERTIFICATE-----
-
Open Okta admin
-
Navigate to “Applications” (Applications → Applications in the left menu)
-
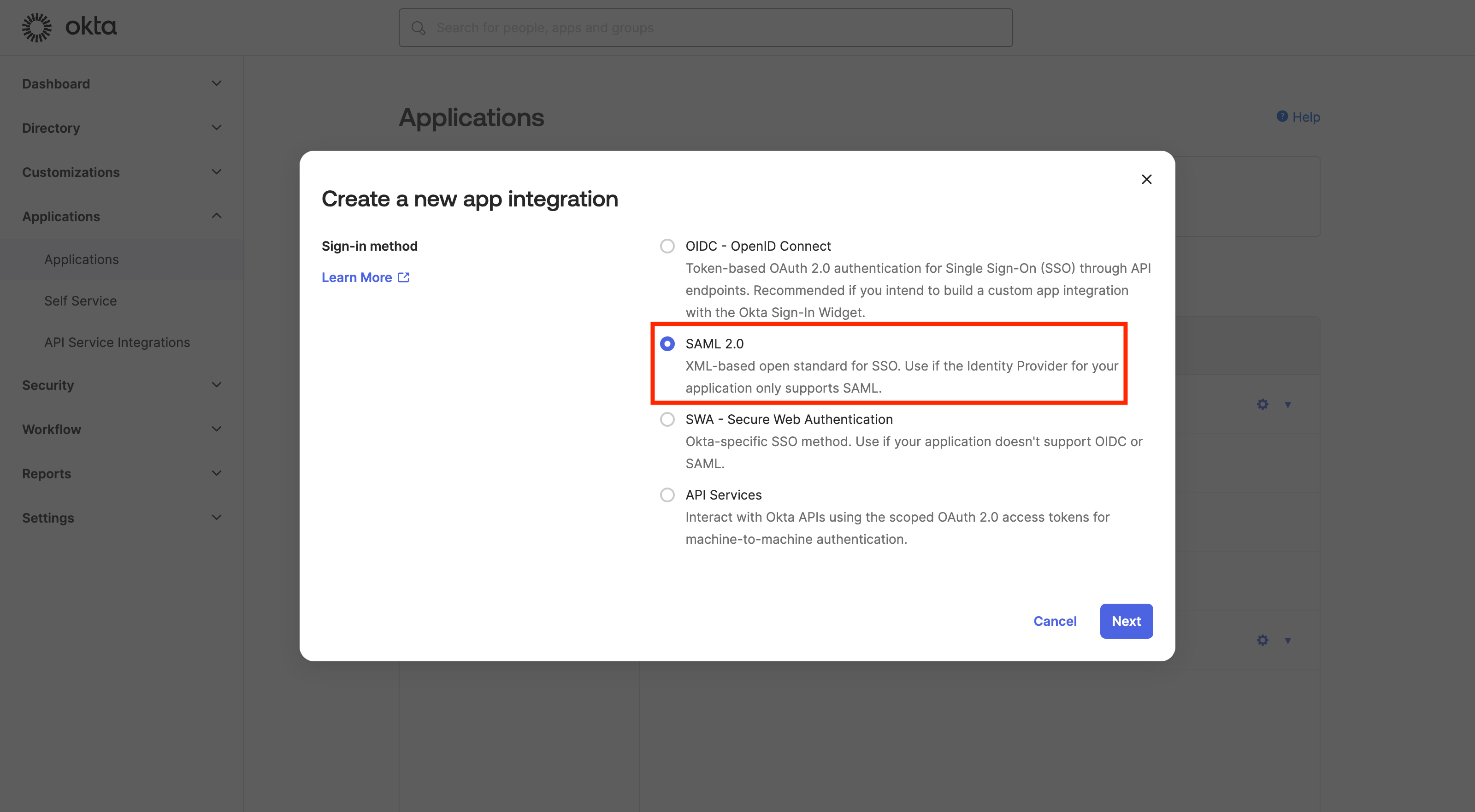
Create a new “App integration” (click Create App Integration)
- Select “SAML 2.0”
- Click “Next”
- Enter “App name” (e.g. MacStadium-SAML)
-
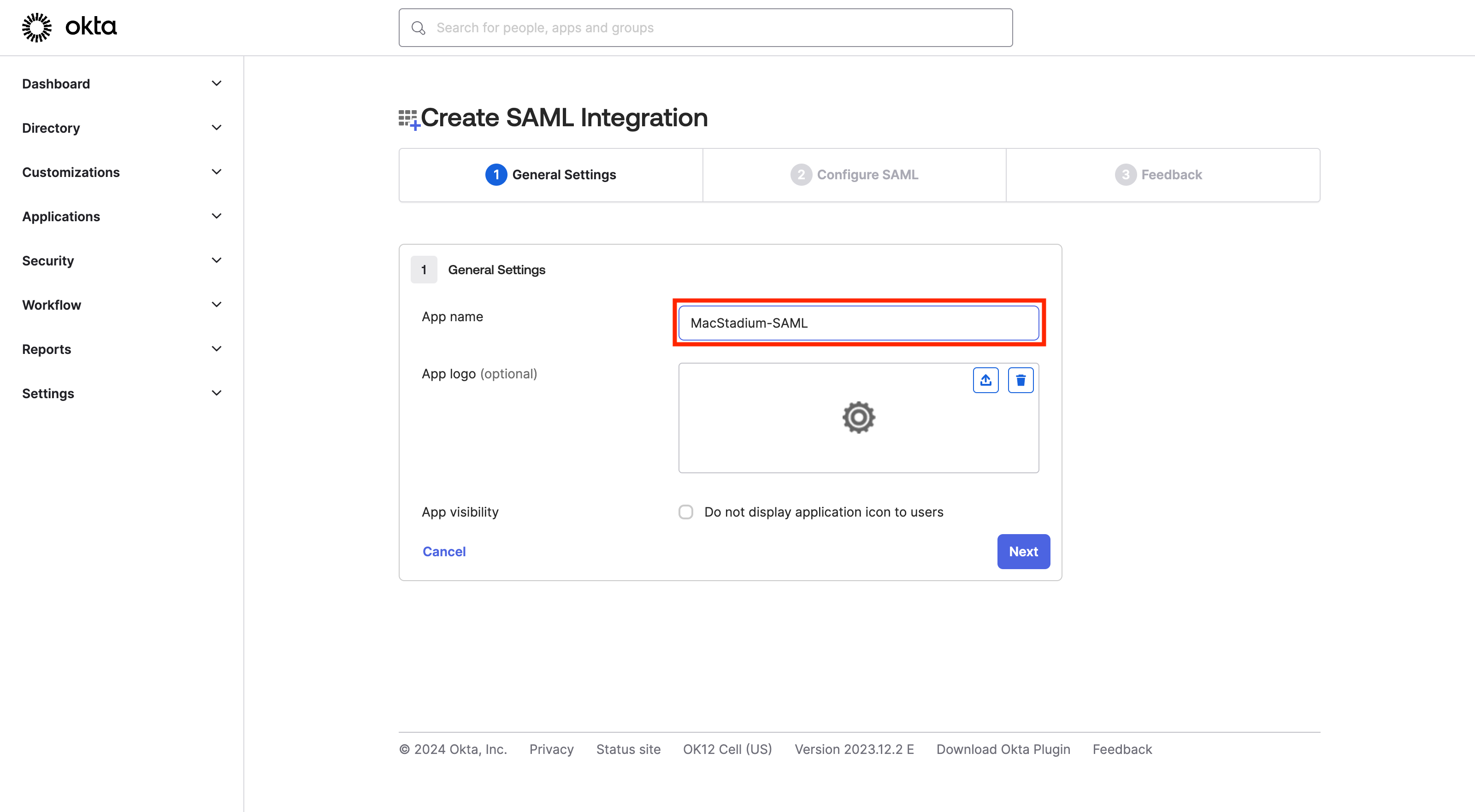
-
Configure the SAML application
-
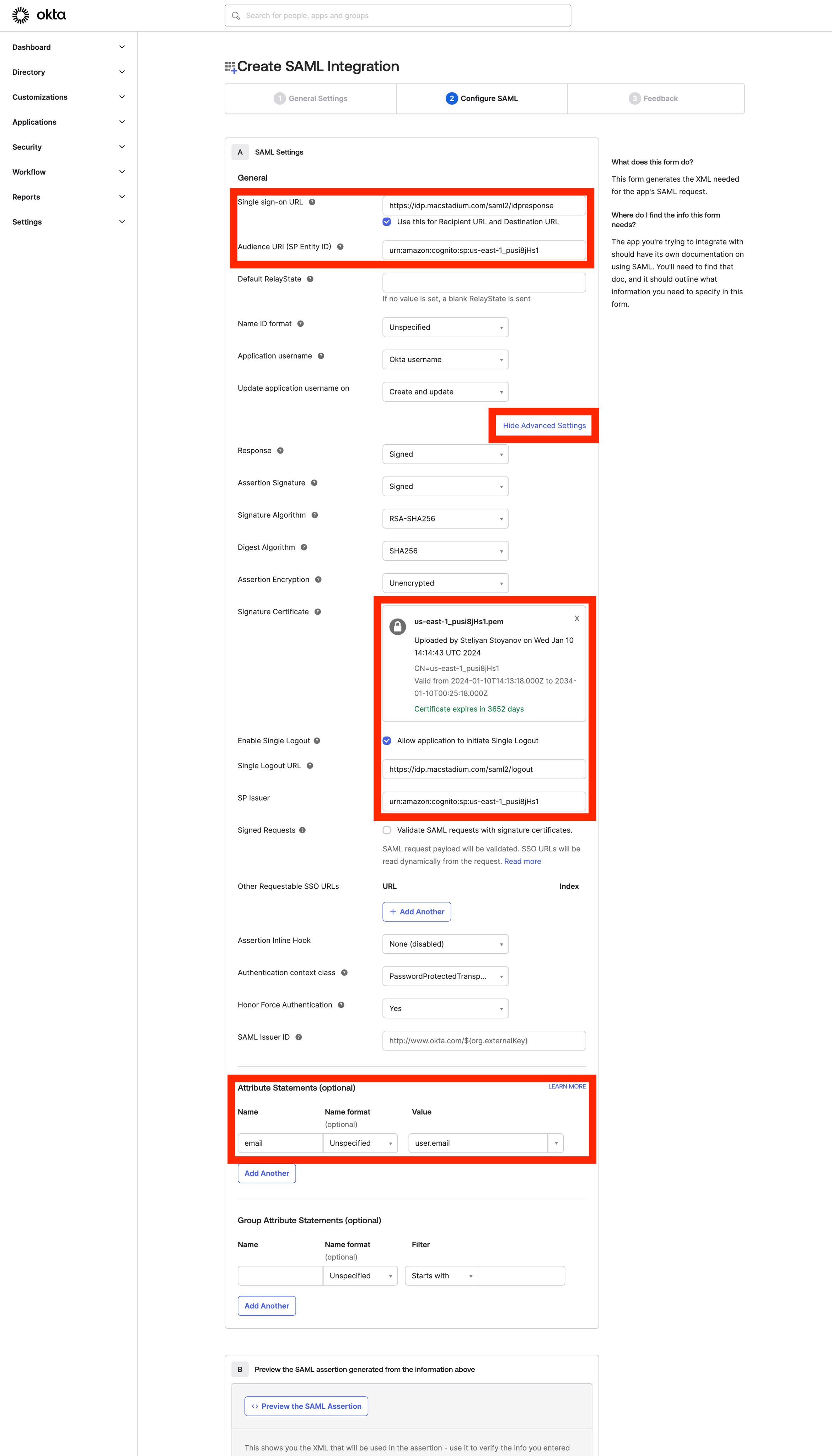
Sign-on URL:
https://idp.macstadium.com/saml2/idpresponse- Use this for Recipient URL and Destination URL: ✔︎ (make sure it’s checked)
-
Audience URI (SP Identity ID):
urn:amazon:cognito:sp:us-east-1_pusi8jHs1 -
Click “Show Advanced Settings”
-
Upload the public certificate (
macstadium-us-east-1_pusi8jHs1.pem) from Step 1 -
Single Logout
- Allow application to initiate Single Logout - ✔︎ (make sure it’s checked)
-
Single Logout URL:
https://idp.macstadium.com/saml2/logout -
SP Issuer:
urn:amazon:cognito:sp:us-east-1_pusi8jHs1 -
Attribute statements
- Map email to user.email
-
-
Complete the setup by pressing “Finish”
-
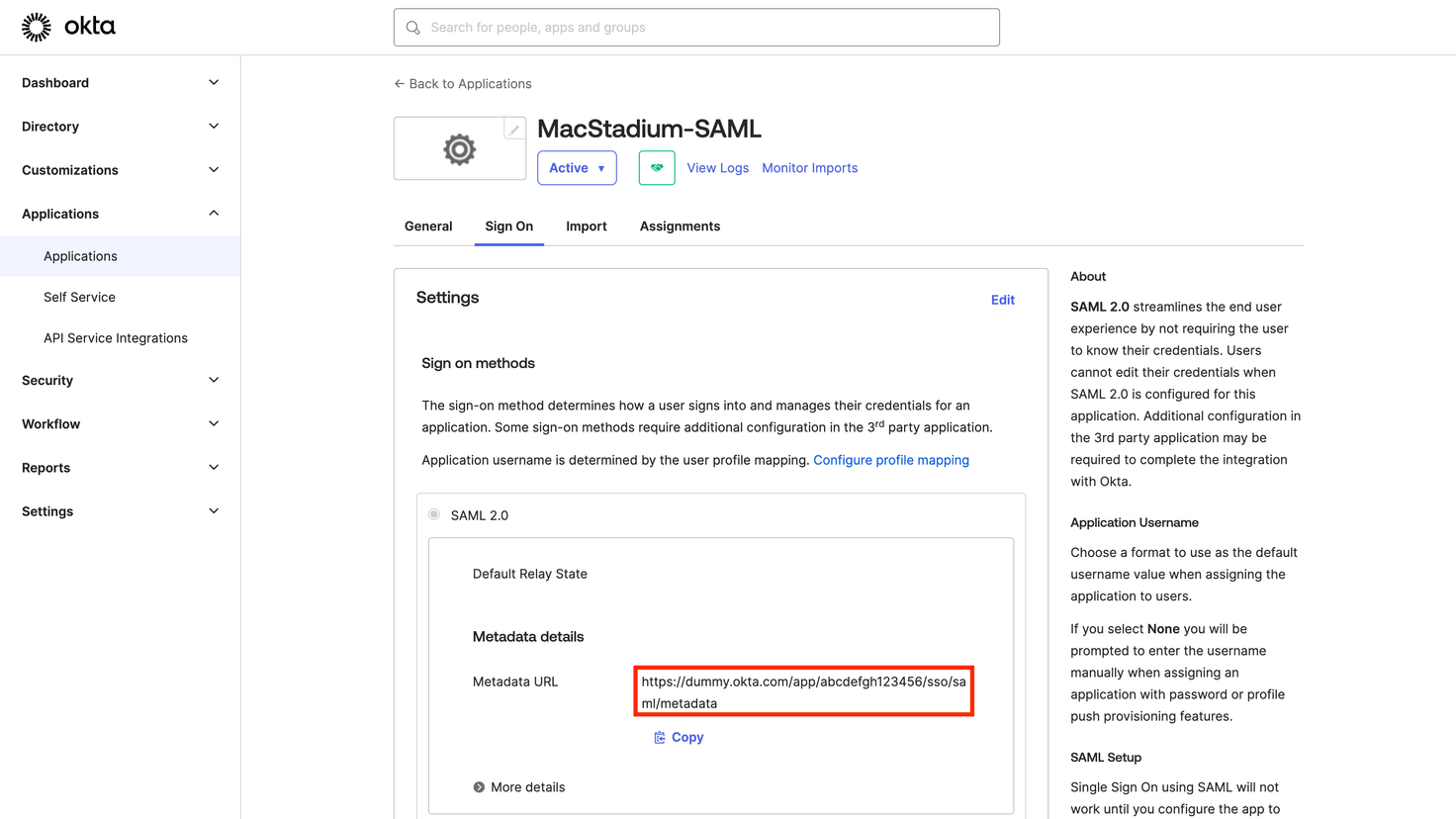
Provide our support team the “Metadata URL”
Updated 5 months ago
