Site-to-Site VPN Configuration with Azure
About
Site-to-Site VPN configuration with Azure allows a secure connection for on-premises networks to Azure. These are some of the benefits of using Site-to-Site VPN with Azure:
- Secure connection Site-to-Site VPNs use encryption to protect data from unauthorized access as it travels over the internet.
- Industry-standard protocols Azure VPN Gateway uses Internet Protocol Security (IPsec) and Internet Key Exchange (IKE) protocols.
- Customizable You can customize site-to-site configurations in various ways, such as BGP, forced tunneling, and network traffic limiting.
Overview
The goal of this documentation is to update the Site-to-Site VPN configuration between Azure and MacStadium ASA firewalls.
To establish a stable and persistent connection between an Azure and the MacStadium private cloud, configure an IPsec Site-To-Site VPN between the two clouds.
Getting Started
Step 1 - Review the IP Plan information and gather the necessary computer and firewall information.
Step 2 - Create a Local User Account on the firewall to manage it.
Step 3 - Set up regular backup / restore testing.
Step 4 - Customize the firewall (for example, allowing IPs to access MacStadium via Internet).
Step 5 - (Optional) Site-to-Site configuration.
Azure Setup Connectivity
Currently, for VPN connectivity between MacStadium and Azure there are two options:
NOTES:
- Active/Active Disabled. Every Azure VPN gateway consists of two instances in an Active/Standby configuration. According to Azure, for any planned maintenance or unplanned disruption that may happen to the Active instance, the Standby instance would take over (failover) automatically and resume the Site-To-Site VPN connections.
- Active/Active Enabled. In this mode, each Azure gateway instance has a unique public IP address and both instances establish an IPsec Site-To-Site VPN to your MacStadium firewall. For this VPN mode, you should also enable the TCP State Bypass feature in your ASA firewall which requires an access-list, class-map, policy-map, and a service-policy. This is a requirement for Site-To-Site VPNs with Virtual Tunnel Interfaces only and is configured to allow asynchronous routing between separate VPN tunnels.
In both VPN modes, static or dynamic routing with BGP is supported between MacStadium and Azure. In this document, BGP routing is used.
NOTE: For more information about general Azure VPN design, see Azure Documentation: .
Creating a Site-to-Site VPN
This is the general process for creating a Site-to-Site, from the Azure private cloud to the MacStadium private cloud.
- Login to Azure.
- Create a Virtual Network Gateway.
- Create a Local Network Gateway.
- Create a Site-to-Site VPN Connection.
Log into Azure
- Log in to the Azure portal with the credentials.
- Confirm the correct account and organization.
Create a Virtual Network Gateway
NOTE: The instructions below assume that there is a configured Azure Virtual Network.
In Azure, the virtual network gateway represents the Azure side of the Site-to-Site VPN tunnel.
- In the search box at the top of the screen, type
Virtual network gatewaysthen select the respective entry in the filtered search results. (Azure filters results as you type.)
- On the Virtual network gateways screen, click Create. (Or Create virtual network gateway, if this is the first gateway).
- Select Subscription.
- Select Resource group.
- Provide a Name and select a Region.
- For Gateway type, confirm VPN is selected.
- For VPN type, confirm Route-based is selected.
- Select your SKU.
NOTE: For more information about the available SKUs, see Azure Documentation: Gateway SKUs.
- Select the Virtual network to be used to send and receive traffic through the VPN.
- For Public IP address, select an existing unused IP address or create a new one and provide a name for it.
- In Availability zone, select Zone-redundant.
- In the option Enable active-active mode, leave it as Disable for an Active/Standby VPN, or select Enabled for an Active/Active VPN mode.
- If Active/Active is enabled, then in the section SECOND PUBLIC IP ADDRESS select an existing unused public IP address or create a new one and provide a name for it.
- In Availability zone, select Zone-redundant
- For the option Configure BGP, select Enabled.
- In Autonomous system number (ASN) use the default value 65515 or, if required, use a different ASN in the private range of 64,512–65,534. This is used as the BGP process number in the MacStadium firewall.
- In Custom Azure APIPA BGP IP address add an APIPA address from the range 169.254.21.X. Example 169.254.21.1. This IP will be used in the BGP configuration in your firewall.
- Click Review + create, review the configuration.
- Click Create, and wait for the deployment to complete.
This might take several minutes. - Check if the virtual network gateway is deployed successfully.
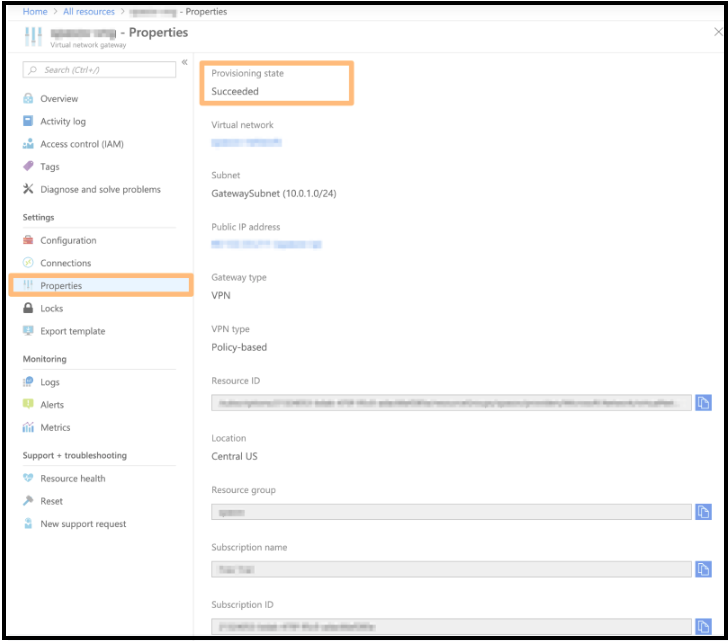
- On the Virtual network gateways screen, select the virtual network gateway and click Properties.
- Verify that the Provisioning state is
Succeeded.
Example: Create a virtual network gateway
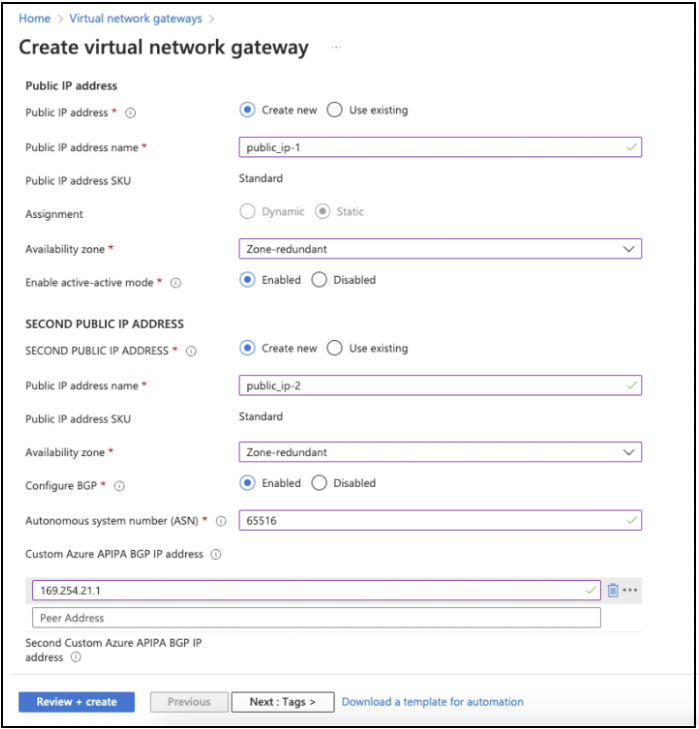
This image shows a sample configuration for a virtual network gateway.
Create a Local Network Gateway
In Azure, the virtual network gateway represents the MacStadium side of the Site-to-Site VPN tunnel.
- In the search box at the top of the screen, type
Local network gatewaysand select the respective entry in the filtered search results. Azure filters results.
- On the Local network gateways screen, click + Create.
- Provide a Name.
- For IP Address, provide the IP address of the public network listed in Appendix B of the https://docs.macstadium.com/docs/ip-plan .
By default, this is the FW1-Outside network.
- Leave Address space empty and click Next : Advanced.
- Set the option Configure BGP settings to Yes.
- Enter the private ASN number to use, for instance 65516.
NOTE: Notice that ASNs 8075, 8076, 12076 (public), 65515, 65517, 65518, 65519, 65520 (private) are reserved by Azure and cannot be used.
- In BGP peer IP address enter the APIPA IP address used in the Azure side, for example 169.254.21.2.
- Click Review + create and then Create.
- Wait for the deployment to complete.
This might take several minutes. When the deployment is complete, the local network gateway becomes listed under All resources.
Create the VPN Connection
After the virtual network gateway and a local network gateway are in place, create and configure the VPN connection between Azure and the MacStadium private cloud.
- In the search box at the top of the screen, type
Virtual network gatewaysand select the respective entry in the filtered search results. Azure filters results. - On the Local network gateways screen, select the local network gateway created earlier.
- From the sidebar menu, select Connections and click + Add.
- Provide a Name.
- Set the Connection type to Site-to-Site (IPsec).
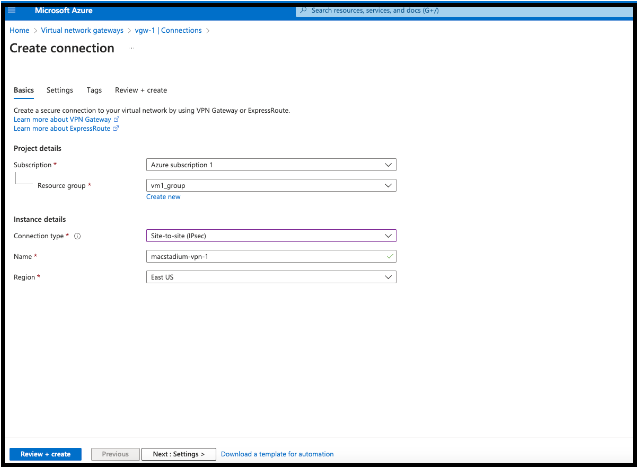
- Select the correct Region and click Next : Settings.
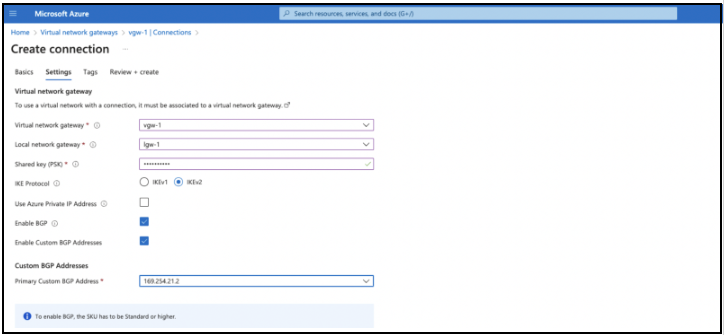
- Select the Virtual network gateway and Local network gateway that were previously created.
- For Shared key (PSK), provide an IPSec pre-shared key.
NOTE: Keep a record of the pre-shared key. It will be used later.
- For IKE Protocol, confirm IKEv2 is selected.
- Select Enable BGP.
- Select Enable Custom BGP Addresses.
- In the Primary Custom BGP Address field, select the APIPA address that were created before.
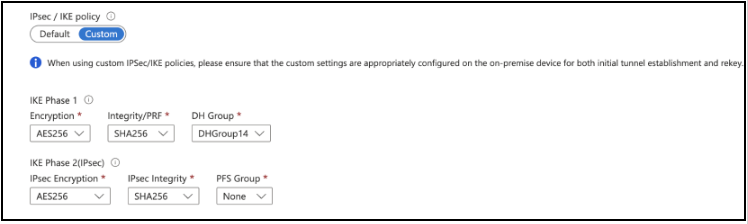
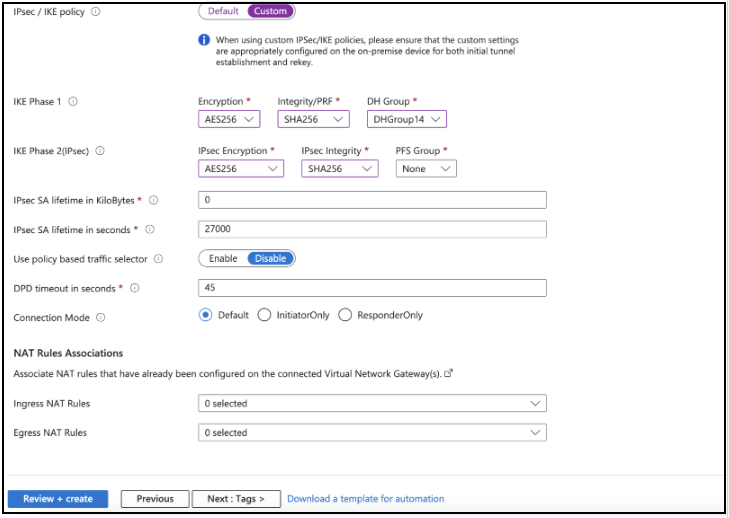
- In IPsec / IKE policy, select Custom
- Set IKE Phase 1 and IKE Phase 2 as follows:
- Review the remaining pre-filled setting and click Review + Create.
- Click Create at the next step.
- Wait for the operation to be completed.
This might take a while. When the deployment is complete, click on Go to resource
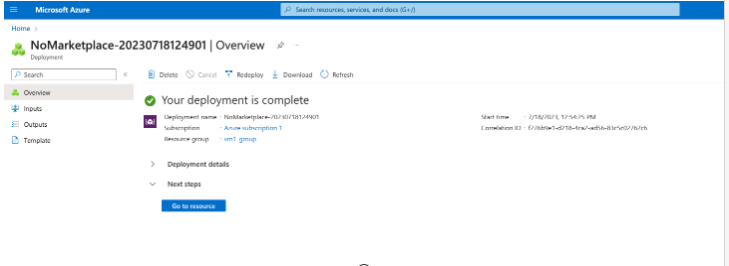
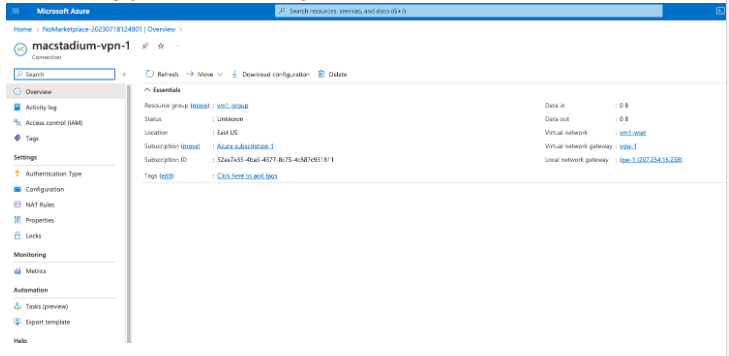
- In the Overview page, select Download configuration:
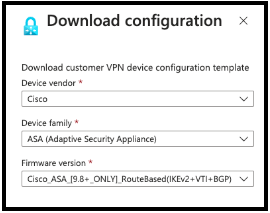
- In the pop-up window, set Device vendor to Cisco, Device family to ASA (Adaptive Security Appliance) and Firmware version to CiscoASA[9.8+_ONLY]_RouteBased(IKEv2>VTI+BGP) and click on Download configuration.
NOTE: The status of the newly created connection is Unknown.
Ensure that Azure Allows Inbound Traffic
Based on the requirements and current setup, it might be necessary to enable inbound traffic from MacStadium to Azure.
NOTE: For more information, see Azure Documentation: and .
NOTE: To proceed with the MacStadium side of the configuration, see https://docs.macstadium.com/docs/azure-preparing-the-vpn-configuration-for-input-into-cisco-asaasav
After creating the Site-to Site VPN connection, configure the Cisco firewall to recognize the connection and let traffic into the MacStadium private cloud. Make sure to downloaded the VPN configuration template from Azure.
Preparing the VPN for Input to Cisco ASA/ASAv
See: https://docs.macstadium.com/docs/azure-preparing-the-vpn-configuration-for-input-into-cisco-asaasav
Configuration Template
WARNING: Without extensive experience with Azure and ASA/ASAv configurations, it is recommended to use a configuration template. Otherwise, the Site-to-Site VPN might not perform as expected.
- In the VPN configuration script downloaded from Azure, the configuration starts after the section below:
- Find the section where the BGP configuration starts.
- Add the MacStadium private network and mask.
router bgp 65516
bgp log-neighbor-changes
bgp graceful-restart
bgp router-id 169.254.21.1
address-family ipv4 unicast
neighbor 10.0.1.254 remote-as 65515 neighbor 10.0.1.254 ebgp-multihop 255 neighbor 10.0.1.254 activate
! NOTE: THE LOCAL NETWORKS TO BE ADDED STATICALLY TO THIS BGP ROUTER NEED TO GO HERE BELOW:
! NOTE: You can add more local on-premises network ranges statically here as well, using the "network" command just like above.
!etc...
! network 10.221.188.0 mask 255.255.254.0
no auto-summary no synchronization exit-address-family
NOTE: Find the MacStadium Private Network by checking that section in Appendix A of the https://docs.macstadium.com/docs/ip-plan .
NOTE: Make sure the name of the interface being used for the VPN connection is Outside as this is the name of the interface in the script downloaded from Azure. If there is a different interface name for the VPN, then make sure to replace all sections where the Outside interface is referenced in the script by the actual interface name being used.
WARNING: Ignore the section, STATIC ROUTING SETUP FOR AZURE, and do not configure any static routes, as BGP will be used instead.
- Access the firewall through SSH using the credentials available in the IP Plan.
- Paste the ASA configuration script and confirm all commands were accepted.
- Use the following commands to confirm if the VPN has been successfully established:
show vpn-sessiondb l2l show crypto ipsec sa
NOTE: For more information, see: https://www.cisco.com/c/en/us/td/docs/security/asa/asa-cli-reference/S/asa-command-ref-S/show-cr-to-show-cz-commands.html
- Save the configuration with the ASA CLI command:
write memory.
Access to the Azure environment from the MacStadium host is now possible (and vice-versa).
NOTE: To feed the complete configuration into your Cisco ASA/ASAv, see https://docs.macstadium.com/docs/setup-macstadium-end .
Updated 10 months ago
