AWS VPN Config for Cisco ASA/ASAv
After you have created your site-to-site VPN connection in Amazon, you need to configure your Cisco firewall to recognize the connection and let traffic into your MacStadium private cloud.
Amazon provides a semi-prefilled configuration file with very detailed instructions. You need to download the configuration file and provide any missing information (indicated by placeholders). Afterwards, you can feed the configuration into your Cisco ASA/ASAv to complete the site-to-site VPN setup.
Download the configuration from Amazon
Amazon lets you download pre-filled configurations for a variety of vendors. The default firewall vendor for MacStadium private clouds is Cisco Systems, Inc.
- Verify that you have created a site-to-site VPN connection in Amazon.
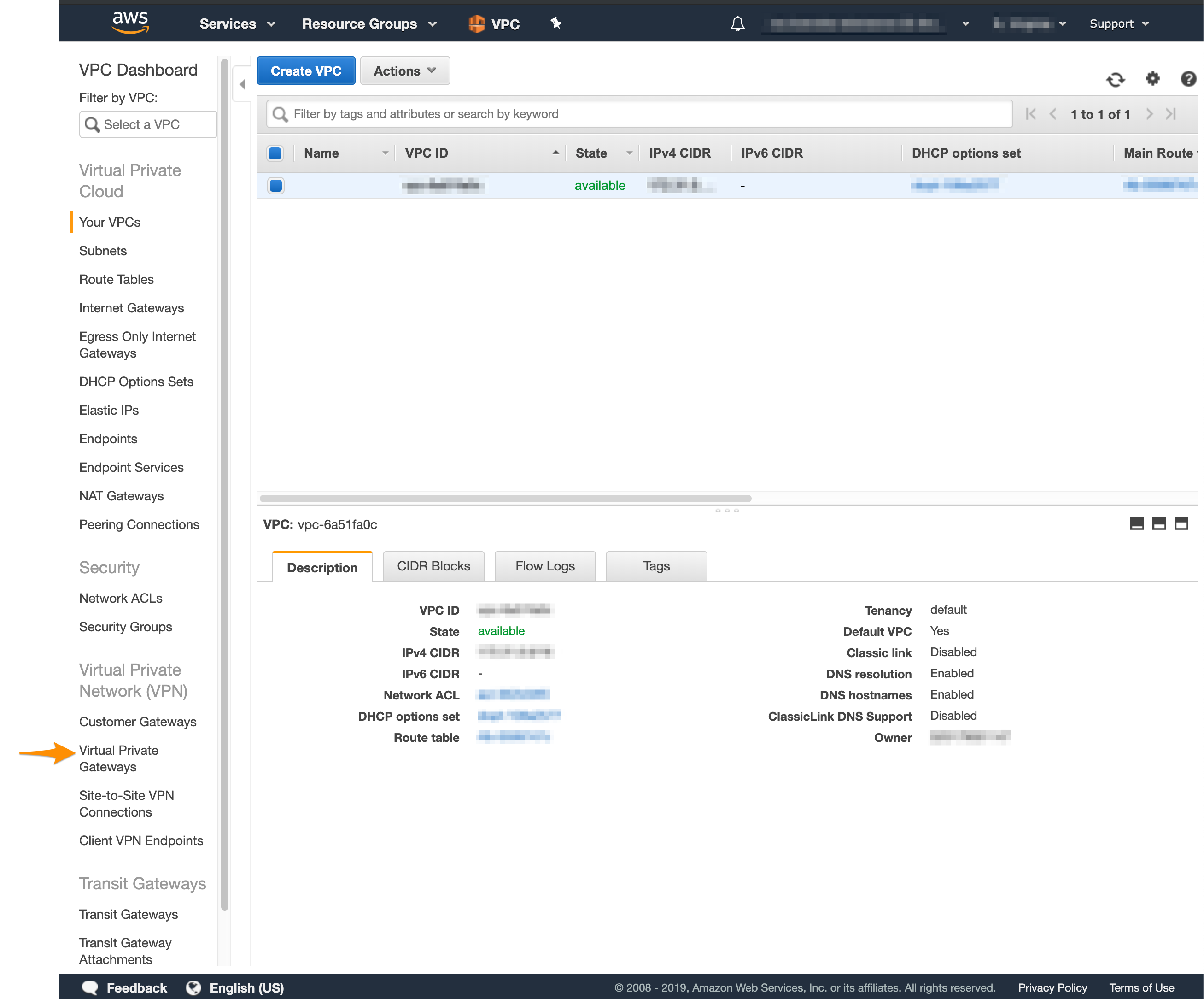
For more information about how to set up your VPN, see Setting Up the AWS Side of the Site-to-Site VPN. - Log in to your AWS Management Console and access your VPC service.
- In the top right corner of the screen, make sure that you're working in the correct region.
- In the VPC service sidebar, locate the Virtual Private Network menu and select Site-to-Site VPN Connections.
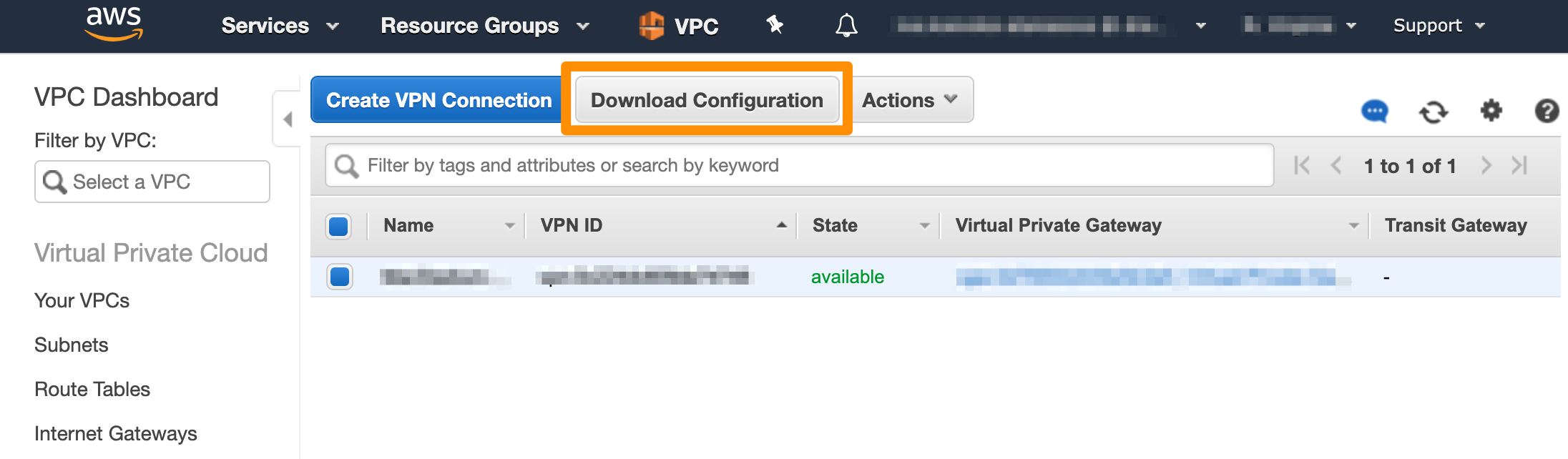
- In the list, select your newly created VPN connection and click Download Configuration.
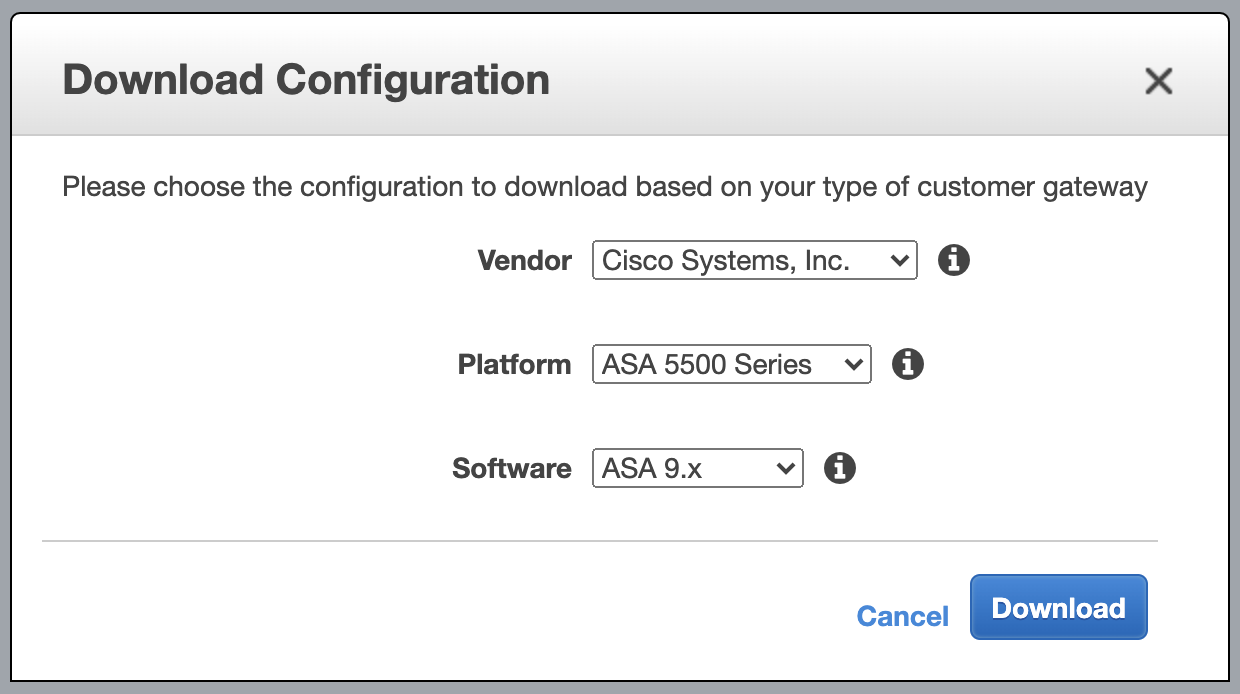
- For Vendor, select Cisco Systems, Inc..
- For Platform, select ASA 5500 Series.
- For Software, select ASA 9.x for a policy-based VPN OR ASA 9.7 + VTI for a route-based VPN.
Fill in the configuration blanks
IMPORTANT: Unless you have extensive experience with AWS and ASA/ASAv configurations, follow the instructions in the configuration file to the letter. Otherwise, your site-to-site VPN might not work as expected.
You need to manually replace the placeholders in the configuration file you downloaded from Amazon with the values for your MacStadium configuration.
Table 1: Configuration parameters
| Placeholder | Description | More information | Example |
|---|---|---|---|
<outside_interface> | The name of the outside interface of your Cisco ASA/ASAv device as provided in Appendix A of your IP Plan. By default, the value is Outside. | The IP Plan | Outside |
<outside_access_in> | A unique name for the access control list that permits the creation of the tunnel and the traffic over it. | Cisco Documentation: Cisco Access Control Lists | outside_access_in |
<vpc_subnet> | The IPv4 address of your Amazon VPC (without the subnet mask bit notation). | You can get this value by logging in to your AWS Management Console, navigating to your VPC dashboard, selecting your VPC, and checking the Description at the bottom of the screen. | 192.168.0.0 |
<vpc_subnet_mask> | The subnet mask for your Amazon VPC. | You can get this value by logging in to your AWS Management Console, navigating to your VPC dashboard, selecting your VPC, and checking the Details at the bottom of the screen. You need to convert the subnet mask bit notation to the correct subnet mask (e.g., the /16 notation converts to a 255.255.0.0 subnet mask). | 255.255.0.0 |
<amzn_vpn_map> | A unique name for the crypto map. If you already have other crypto maps configured, you need to change the mapping number. | Cisco Documentation: Configuring Crypto Maps | amzn_vpn_map. |
<sla_monitor_address> | An IP address in your Amazon VPC that can serve as an SLA monitor keeping the site-to-site tunnel alive. | You can set this to the <vpc_subnet> address plus one. For example: if your <vpc_subnet> is 192.168.0.0, use 192.168.0.1 for your <sla_monitor_address>. | 192.168.0.1 |
<local_subnet> | The IP address for the internal private network of your MacStadium cloud as provided in Appendix A of your IP Plan. By default, this is the Private-1 network. | The IP Plan | 192.168.0.0 |
<local_subnet_mask> | The subnet mask for the internal private LAN of your MacStadium cloud as provided in Appendix A of the IP Plan. By default, this is the Private-1 network. | The IP Plan | 255.255.0.0 |
- Verify that you have downloaded the configuration file from your AWS Management Console.
- Open the configuration file.
- Replace all placeholders with their respective values. Use Table 1: Configuration parameters for reference.
- Uncomment the line:
access-list amzn-filter extended permit ip .... To uncomment, remove!at the start of the line. - Uncomment the lines for
objectandnatconfiguration at the end of the config file. To uncomment, remove!at the start of the line. - Keep the following line. This ensures the SLA monitor works as expected.
object network obj-SrcNet
subnet 0.0.0.0 0.0.0.0
Note that based on your network configuration and requirements, you can modify this line to map to the subnet and the subnet mask for the Private-1 network from your IP Plan. If you choose to modify this line, do not configure the <sla_monitor_address> value.
- On the following line, change
0.0.0.0 0.0.0.0to a combination of the IP address and the subnet mask for your Amazon VPC.
You can get these values by logging in to your AWS Management Console, navigating to your VPC dashboard, selecting your VPC, and checking the Description at the bottom of the screen. You need to convert the subnet mask bit notation to the correct subnet mask (e.g., the/16notation converts to a255.255.0.0subnet mask).
For example:
object network obj-amzn
subnet 0.0.0.0 0.0.0.0
TO
object network obj-amzn
subnet 192.168.0.0 255.255.0.0
- On the following line, change
insideandoutsideto the names of the internal private network and the outside interface of your MacStadium private cloud, respectively, as provided in Appendix A of your IP Plan. By default, these arePrivate-1andOutside, respectively.
nat (inside,outside) 1 source static obj-SrcNet obj-SrcNet
destination static obj-amzn obj-amzn
TO
nat (Private-1,Outside) 1 source static obj-SrcNet obj-SrcNet
destination static obj-amzn obj-amzn
- (Optional) Delete the remaining commented lines to clean up the file. Commented lines are indicated by
!at the beginning of the line. - Save your changes.
Next steps
If you are ready to feed the complete configuration into your Cisco ASA/ASAv, see Setting Up the MacStadium Side of the Site-to-Site VPN.
Updated almost 5 years ago
